Supreme Tips About How To Detect Dos Attack
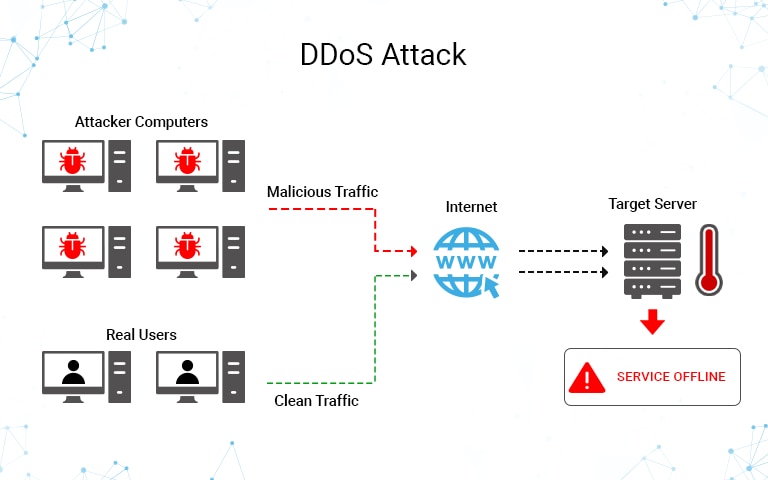
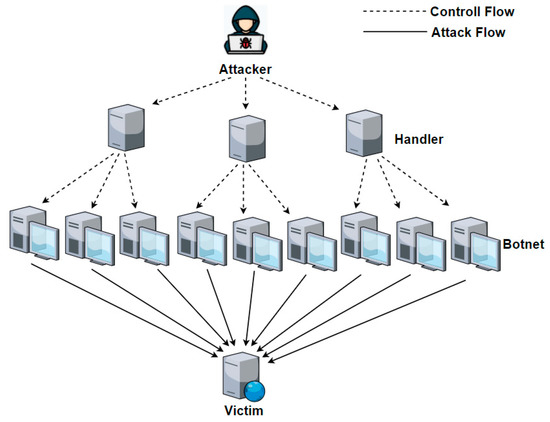
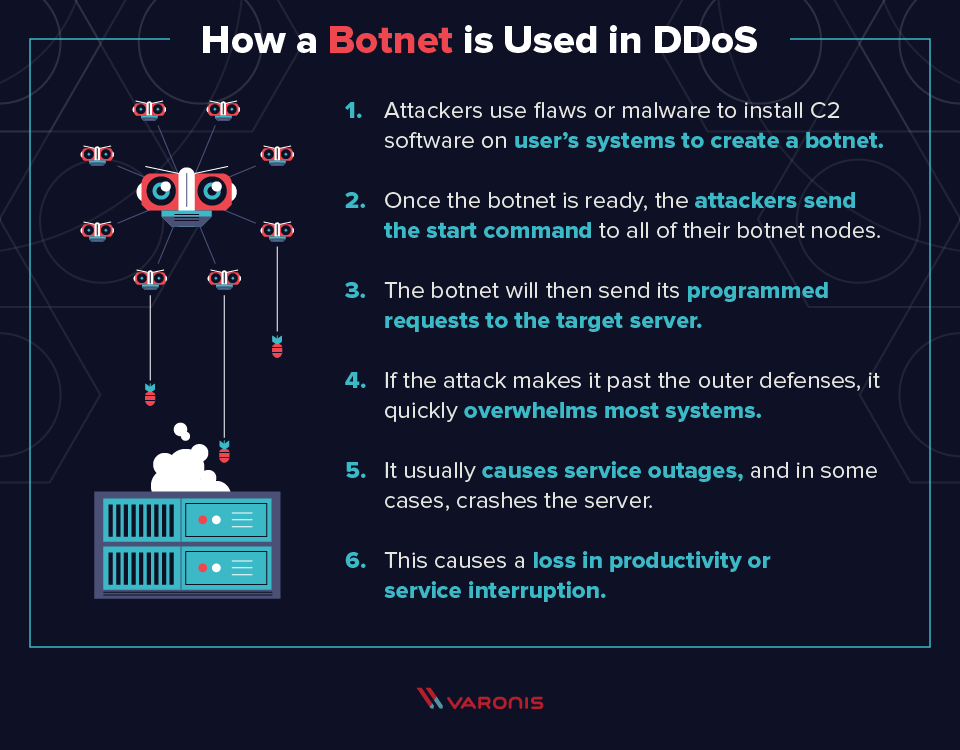
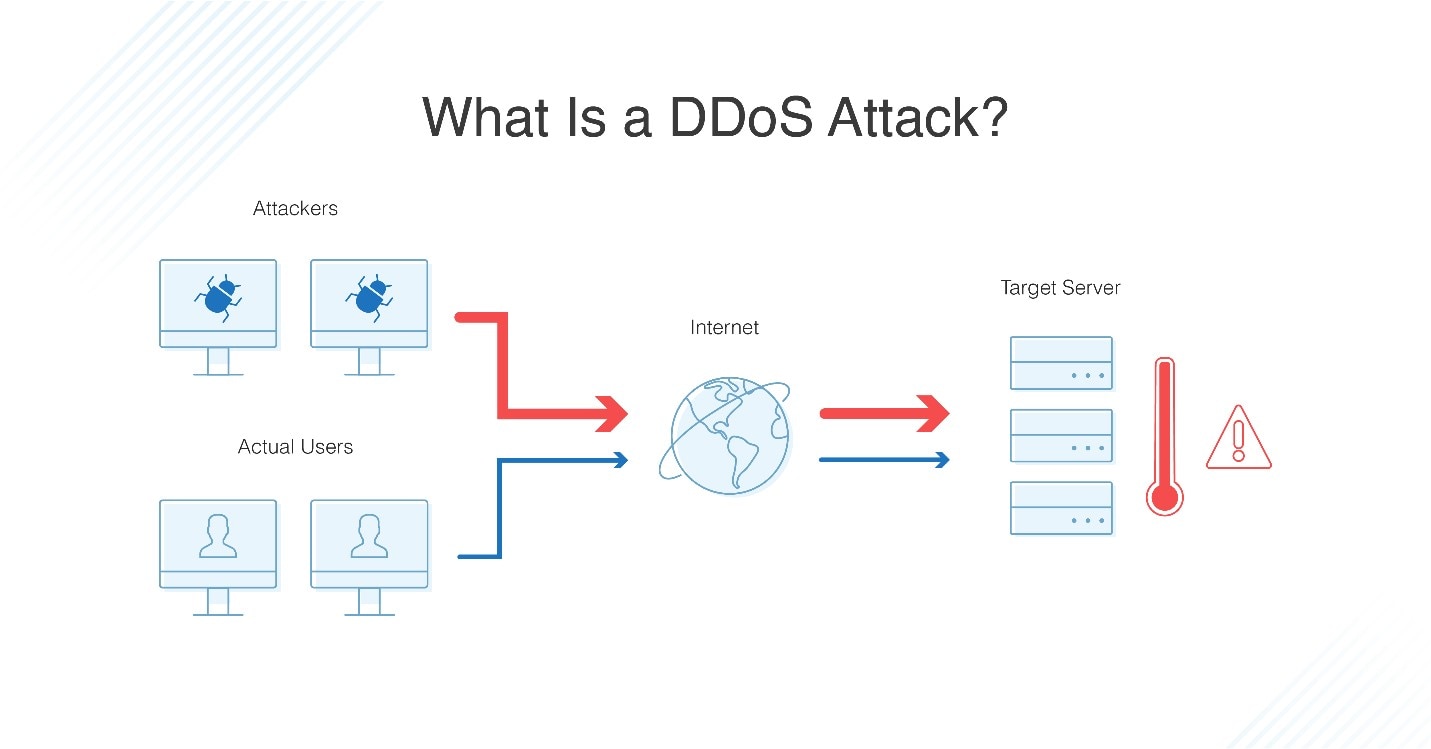
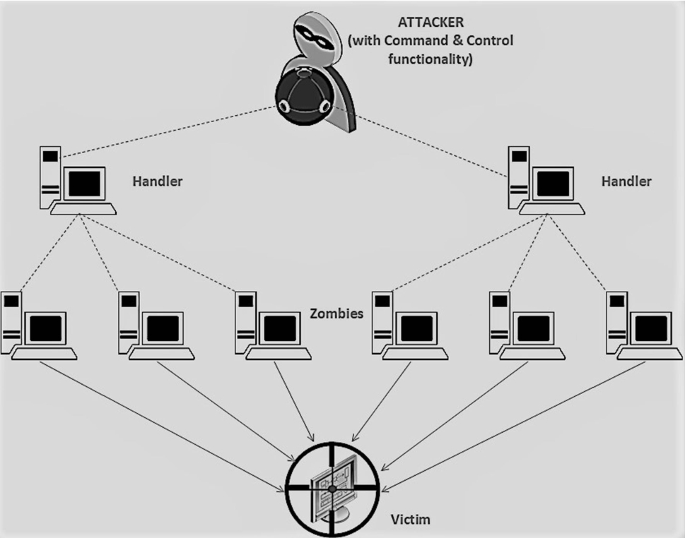
Actually ddos attack is a bit difficult to detect because you do not know the host that is sending the traffic is a fake one or real.
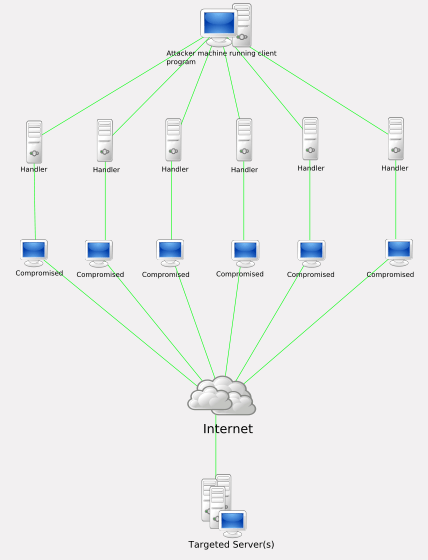
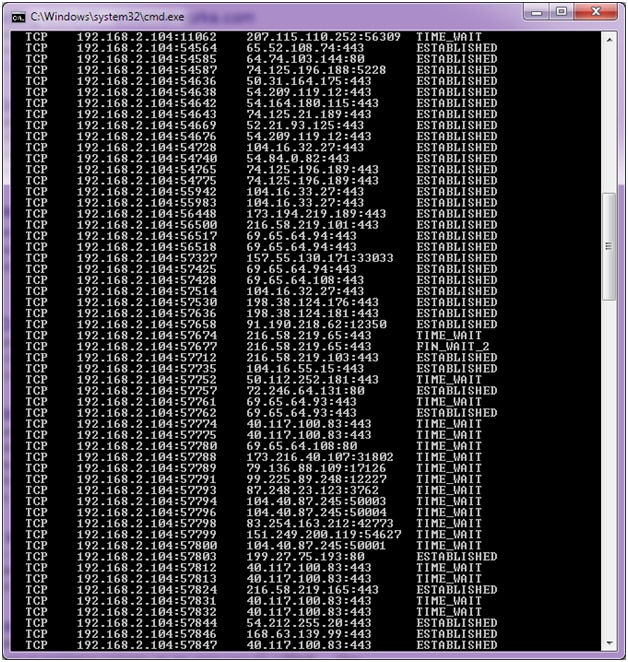
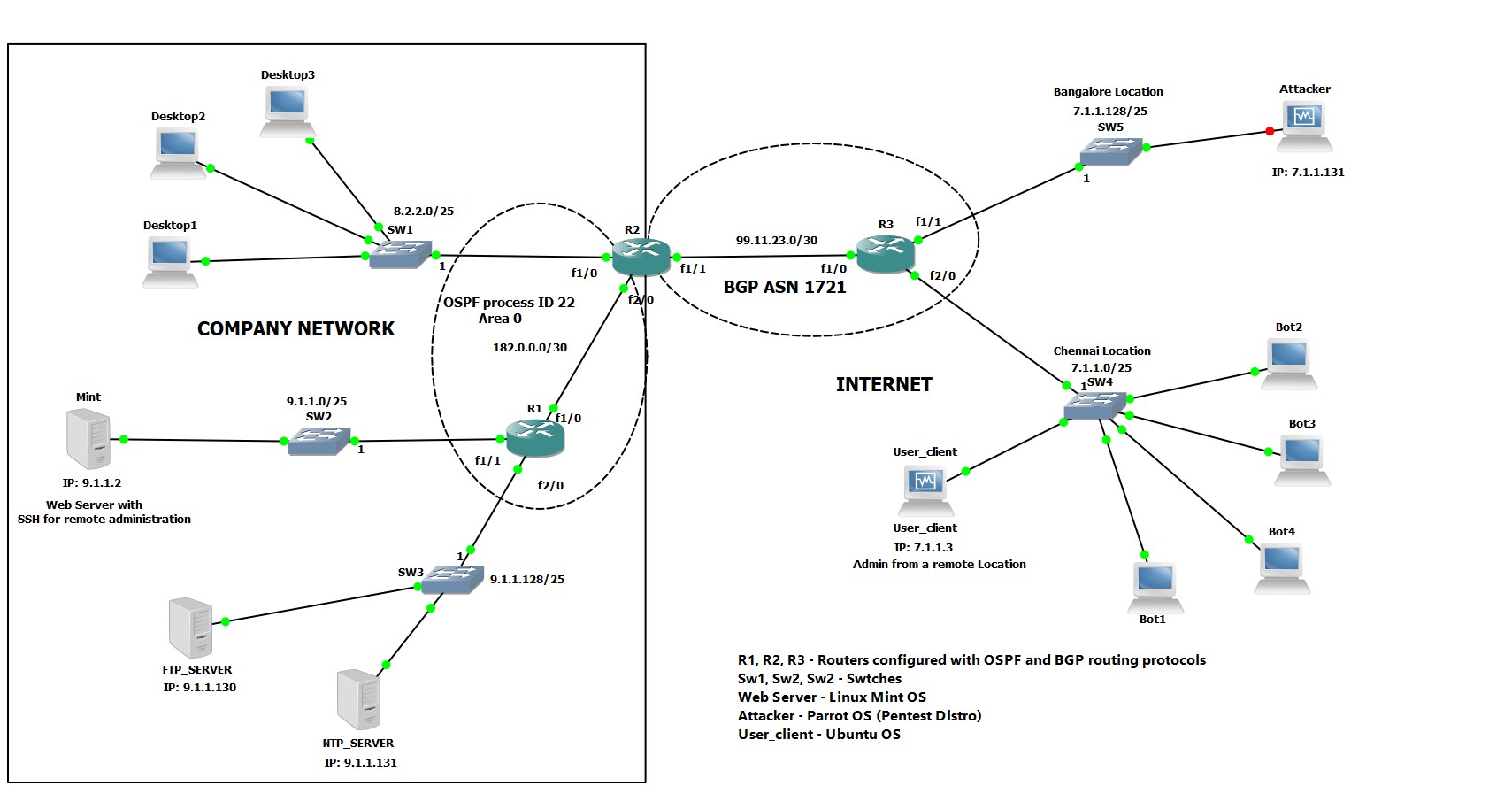
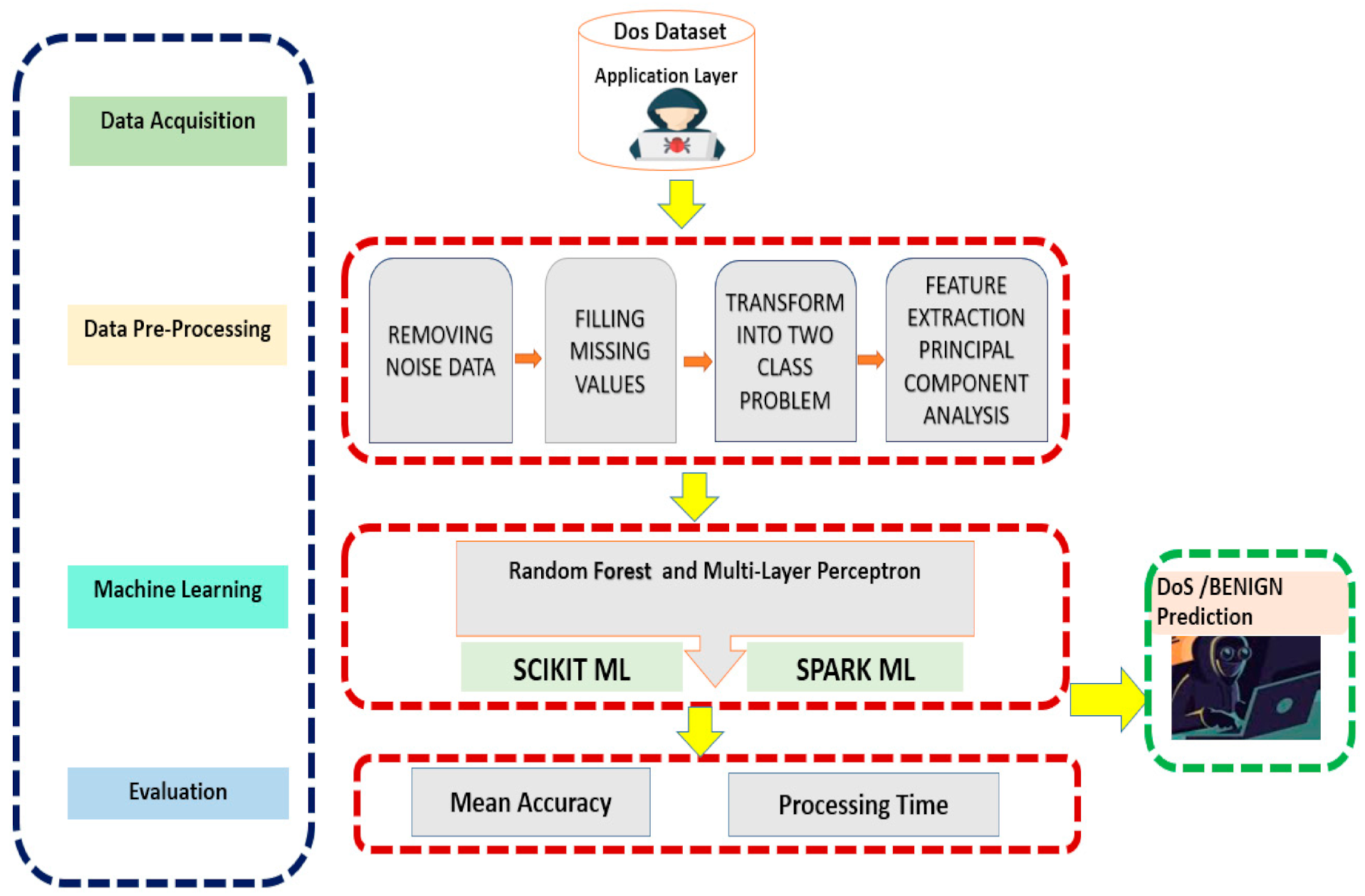
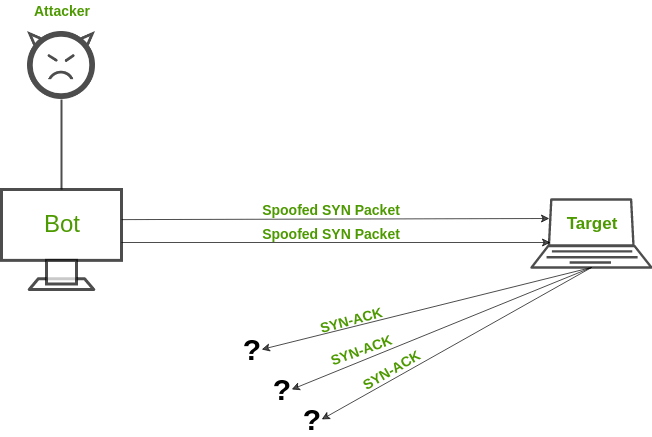
How to detect dos attack. Click server manager in the task bar. This is a video on performing a dos attack with hping3 and detecting the dos attack on the victim machine using kali linux. The python script given below will help detect the ddos attack.
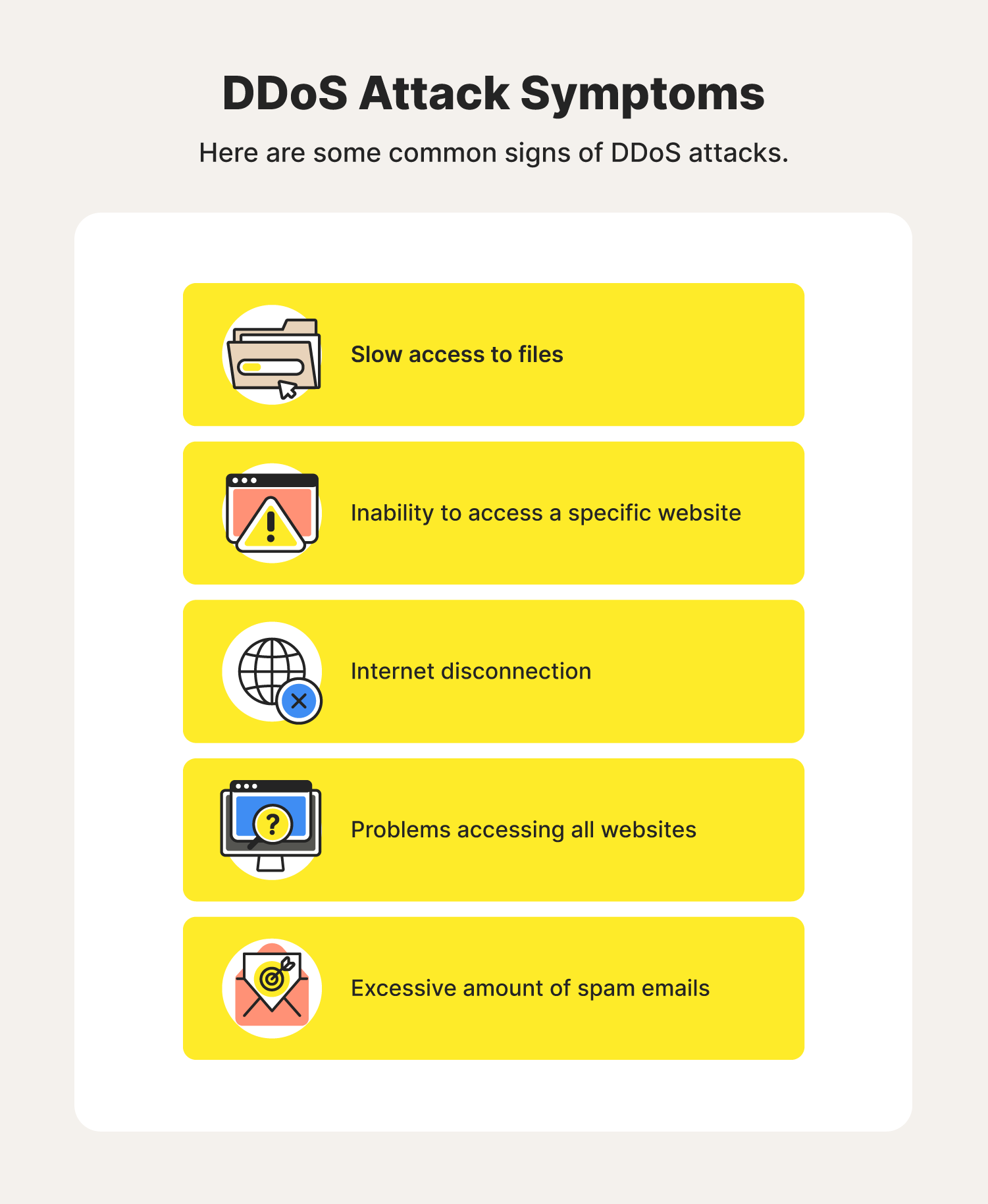
To detect an attack, one has to gather a sufficient network traffic information,. While there’s no one way to detect a ddos attack, there are a few signs your network is under assault: You see a surge in web traffic, seemingly out of nowhere, that’s coming from the same.
Here are some more useful tips on how to identify a ddos attack. While searching the site, results will show that the. Dns uses two types of packets:
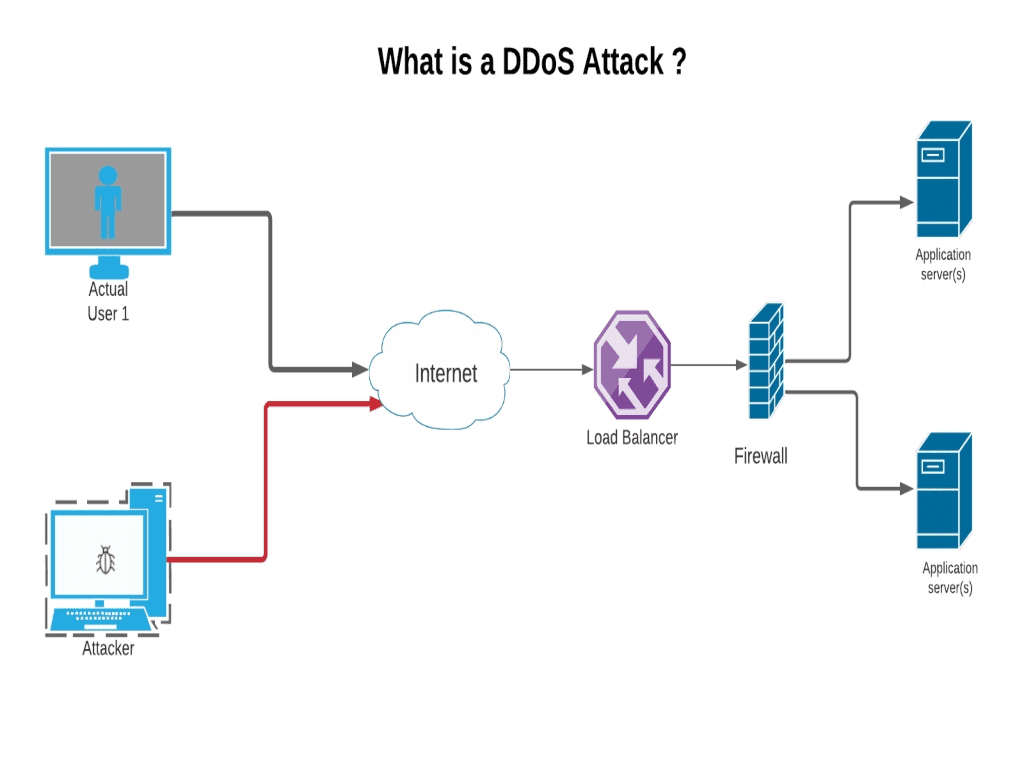
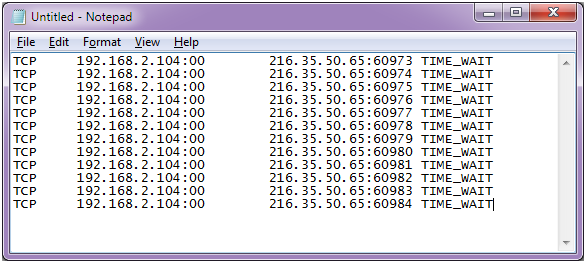
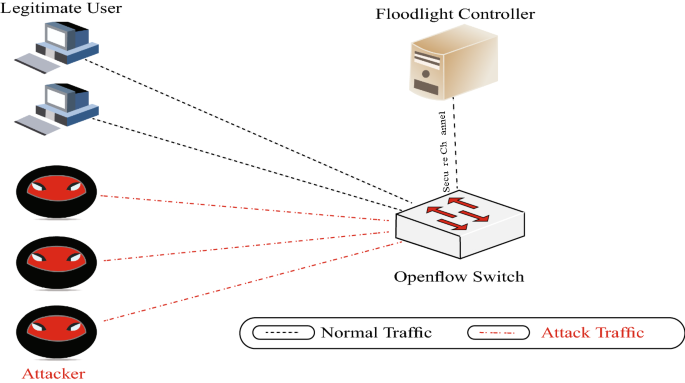
The best way to detect and identify a dos attack would be via network traffic monitoring and analysis. The first step in avoiding or stopping a ddos attack is knowing that an attack is taking place. Network traffic can be monitored via a firewall or intrusion detection.
Detecting an active dos attack when a server is attacked by ddos, it slowly starts killing it’s performance. You can view this by logging into your account with your web host and opening cpanel. If you are using linux.
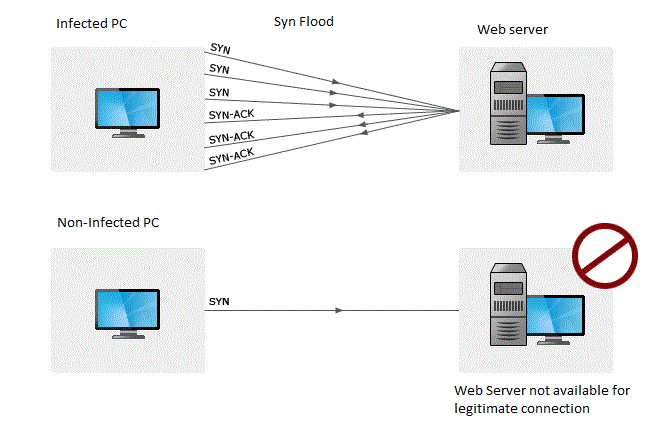
There are techniques for intrusion detection, and of course dos attack, in which for each packet (or flow) some features are calculated, then. To learn how to create rules in the windows server to increase security against ddos attacks, pay attention to the following: How do you detect dos attack when opening any file or trying to access that site, it will give slow network performance.